Wearable Technology Research Essay
Executive summary
BlackWing management received an approval for the planning phase of the new wearable technology. Being a private company that offers transportation to individuals not only in government but other sectors as well, it is only practical to keep up with advancements in technology that would not only make work easier but also play a role in the early identification of threats to their clients. The overall goal of the new wearable technology is to create a synchronization system between the employees which goes a long way in guaranteeing top-notch service delivery. BlackWing acknowledges that the world is changing and the company should embrace change not only for the present crop of employees but also for the future workers.
A. Description and justification
The main wearables that will be used by the BlackWing transportation agents are smartwatches, trackers, Bluetooth-enabled headsets and implantable devices. All these devices are connected via Bluetooth to the wearer’s Android phone but they are tracked via GPS systems from the main control room.
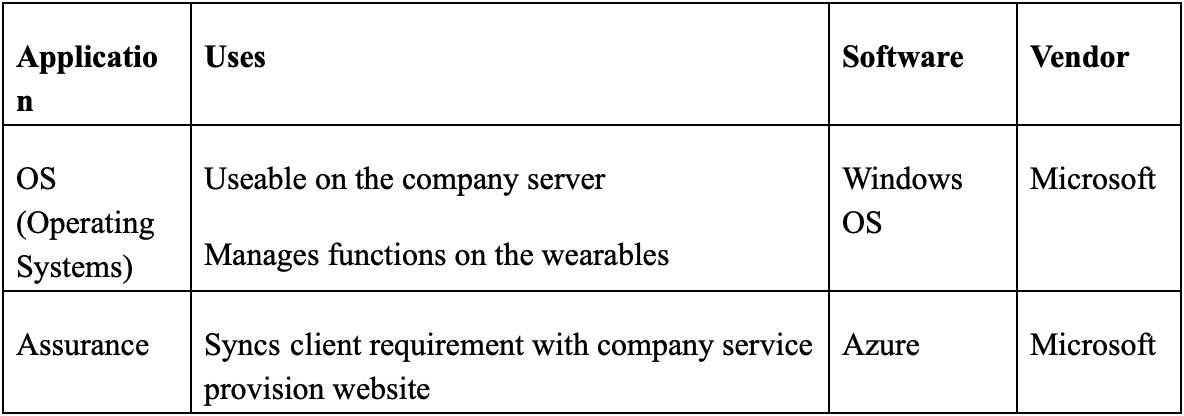
Operating systems
These are written, synchronized and updated by Microsoft. The justification for this is that the systems provider is not only dependable but also offers timely updates that are necessary for the smooth running of the company. In addition, Microsoft runs seveal software that plays a major role in cloud computing because they are flexible and available for systems of all bitrates (Starner 2014). It enjoys the monopoly that accompanies being a dependable service provider.
Assurance
BlackWing’s clients are politicians, senior businessmen and some mid-level players in the business and political field. Azure is a software that is also a cloud computing platform. It is a hybrid, therefore allowing for multiple usages and heavy data sustenance. This comprehensive tool is used by IT professionals to manage the different applications that are on the smartwatches and to track the in-ear headsets. The other benefit of this is that it is large scale and updates are regular to accommodate the shifts in internet demographics and demands. The service provider for this remains Microsoft and its core is the binding of devices that can connect to the internet, ensuring privacy and extending efficient service delivery.
B. Data requirements
All the wearable devices use batteries, thereby reducing the risk of damage through electrical circuits. The smartwatches consume more data than the other wearables because the agents are in constant communication with clients. The others are tracked by GPS from the control room. The sensors in the wearables consume up to thirty percent of data, depending on geographical location (Lucero, Clawson, Lyons, Fischer, Ashbrook and Robinson 2015).
These applications are not only simple but work on the same levels as a basic iPhone. However, there are sensitive strips that were soldered into the earpieces and smartwatches. In addition, the conference presented opportunities for the utilization of nanotechnologies such as the skin grafts. This may be considered a possible breach of privacy but when working in such an enterprise, taking precautions is necessary (Bhushan 2017). The nanotech uses the body’s readings to send information. The grafts will be placed on the arm, where they blend with the skin and can only be taken off when assignments have been completed.
C. Technology architecture
Infrastructure
Cloud computing remains the biggest avenue for crowdsourcing in the present and in the future. All functions of the wearable technologies at BlackWing will be dependent on the stability of the Cloud and the service providers. Monitoring and evaluation processes will be carried out through the GPS functions and results tabulated for client analysis (Rittinghouse and Ransome 2016). This will not only allow for cost-cutting but will reduce the time that is spent on collection and analysis before sharing with the clients. Azure is not only flexible but also guarantees maximum security.
Principles
The wearable devices work on the principle of reliability and efficient service delivery. There have been incidences in the past where the preferred method of collecting client information caused a snarl up that led to the loss of valuable data as well as clients. The older systems made it difficult to track the vehicles as well as the persons who had contracted BlackWing’s services.
The software
Wearable technology entered the market with the FitBit which is used by the wearer to keep track of their fitness levels. The smartwatches, earpieces and implants which will be used by BlackWings use a lot of data because of the nature of business. The servers at the company are adjusted to ensure that they can handle incoming and outgoing traffic while remaining linked to the cloud. It is likely that the devices will get smaller in the future. User experience will be maintained by providing second by second backup which retains all information that was initially input in case the internet is down at one point. The software will also go a long way in enabling BlackWings reduce its carbon footprint in form of paper while working towards the other goals (Zheng, Xie, Dai, Chen and Wang 2017).
D. Work breakdown
The rolling out of the new technology is scheduled to take place in two main phases; the application and implementation of standards. These two will signify the commencement and closing of the same while those in between will be standard procedure. In preparation, the IT department will ensure that BlackWing’s systems are compatible with the wearables as well as make the necessary adjustments. Standards implementation involves ensuring that the specific cloud can be accessed only by the clients and not by third parties. In between the two, the department will ensure that the firewalls can withstand an attack without breach.
E. Activity timeline
Like ordinary activities, the purchase and use of the wearable devices is a project with different phases that check for progress. Every stage is dependent on the other. The procurement department has to place an order for the devices as well provide the geographical circumference of operation. The second phase involves training the staff members on how the wearables work. This is done by using simulations and PowerPoint presentations. As the specialist in charge of the digitization project, it would be necessary to use the samples that were brought from the conference. The third phase involves carrying out a test run to determine preparedness and effectiveness of the gadgets.
Finally, the concerned department ensures that the gadgets are delivered and synchronized for use. The possible challenge with this is an absence of communication between the tech company, the software vender and BlackWings. The members may also cite reasons such as being unable to operate the smartwatches or sensitivity to the skin graft nanotechnology. When the devices are brought in, synchronization and connection to the specific cloud will be done in five business days during which all members will be given specific access codes and GPS trackers activated for efficient service.
F. Critical success factors
The main factors here include the kind of leadership in place when the technology use begins. They need to be not only supportive but also accommodative of the errors that may occur. Second, all members of the team are required to play an active role in learning the intricacies of the wearables and the Cloud functionality. Third, the gadgets are expensive and financial support will be required. All investments require sufficient capital. Effective monitoring and control is also a factor as it will prevent the personalization of company property by members of staff. This is done by the main control room (Alreemy, Chang, Walters and Wills 2016).
G. Stakeholder management
The stakeholders affiliated to this project are the clientele, the investors, the staff and other third parties. All of them have different needs that are fulfilled in different ways by the company. It is necessary to identify the stake that each of them has towards the adoption of ths new tehnology as this will inform most of the decisions made at board level. A successful introduction of cloud computing is only as effective as those who desire to see the change. It is expected that there will be some opposition but as Eskerod and Jepsen put it, all opposition can be managed and a workable compromise adopted (2016).
The introduction of the wearables should be communicated to each stakeholder so that they can identify the possible problems and help push the company forward. In the event that the response will be less favorable, the board has to address the arising issues before the project procedes to the next phase. They will be notified of the expected changes, benefits and also the possible challenges.
H. Cost and budget management
Given that the company management already approved the rolling out of this program, consideration must be taken for the professionals who will be hired to train the staff members and to guide the IT department on how to identify malware which would cost the business massive amounts of money. Currently, these costs can be accommodated because there have been budget cuts in the last few months whose aim has been to not only create a leaner workforce but to also reduce the time taken in service delivery. By embracing cloud computing, this vision is guaranteed at half the cost of previous methods.
I. Pre-implementation plans
The commencement of this project is when the training of technical staff and customer service agents is carried out by the responsible team. The gadgets will be used on a test run to determine the effectiveness and dependability of the same. This will prevent the occurrence of glitches as well as issues related to accuracy. The finance department needs to prepare the required sums to prevent a backlog. The IT department will keep monitoring the devices for updates on software and security protocols. Technical staff in this department are required to not only update the cloud details but to check that no virus is present.
The key performance indicators are identified at this point so that the company has a progress chart to influence the next course of action. Other plans include the study of the user matrix before technology. This will help in gauging whether the general goal of acquiring the wearable technology has been achieved or it has been to a disadvantage
J. Post-implementation plans
The same department is still charged with maintaining user experience and seeing that the cloud vendor keeps the company abreast of all future changes. The cloud will be active with commands and outgoing data which will weigh heavily upon the company but it can be managed. Regular reporting will be required from all staff members who transact businesses on behalf of the company. This will be helpful in facilitating feedback and coming up with new ways of service delivery.
It should also be noted that not all complaints arising from the use of wearables will be handled by the department. An analysis will be done regarding the level of threat posed by the raised concern and the necessary steps will be taken. Monitoring and evaluation will continue and reports presented quarterly for analysis and possible recommendations. The monitoring department is charged with the collection of data from here on, unless otherwise indicated.
K. Risk management
Change is inevitable and BlackWings worked on a strategy to ensure that incorporating new technology into the daily routine will not cause a slack. All departmental managers need to be acquainted with strategies aimed at reducing risk while keeping the workforce intact. Cloud computing can be tricky especially for those who are not technologically savvy. Attention to detail should be accorded the staff who may be facing challenges. It is possible that some of them may choose to stop working the company routes when they do not understand how the GPS locator works (Booth 2015).
Second, the shift towards this technology was prompted through the changing market and the addition of younger clients. Instead of firing the older workers, duties should be assigned to them where their services are still important. They are the most at risk and BlackWings management needs to rectify this by assigning them to routes where the clients are not too demanding as this may pile unnecessary pressure on them. The technical staff should be trained regularly to prevent connection or locator mishaps within and without the business space.
L. Recommendations
Information technology is highly sensitive and this not only calls for the ethical handling of the equipment but an empowerment of the individuals who deal directly with the clients. Given that BlackWing deals with transportation, the security measures need to be upgraded alongside the technology.
The company has various sublevels all of which need to be streamlined so that there is no breakdown in communication from the top management and within the departments that are directly involved.
Conclusion
As a private company, BlackWing has competitors in the public and private sector. Upgrading the communication systems is a step forward in getting more clientele. Wearable devices are only as functional as the service provider managing the systems. This is an indication for both parties to share information and recommendations for better service delivery and a better control of the market. Technological developments are inevitable and the company needs to embrace the change or it loses out on profit.
References
Abdinnour, S. and Saeed, K., 2015. User perceptions towards an ERP system: Comparing the post-implementation phase to the pre-implementation phase. Journal of Enterprise Information Management, 28(2), pp.243-259.
Alreemy, Z., Chang, V., Walters, R. and Wills, G., 2016. Critical success factors (CSFs) for information technology governance (ITG). International Journal of Information Management, 36(6), pp.907-916.
Bhushan, B. ed., 2017. Springer handbook of nanotechnology. Springer.
Booth, S.A., 2015. Crisis management strategy: Competition and change in modern enterprises. Routledge.
Eskerod, P. and Jepsen, A.L., 2016. Project stakeholder management. Routledge.
Lucero, A., Clawson, J., Lyons, K., Fischer, J.E., Ashbrook, D. and Robinson, S., 2015, April. Mobile Collocated Interactions: From Smartphones to Wearables. In Proceedings of the 33rd Annual ACM Conference Extended Abstracts on Human Factors in Computing Systems (pp. 2437-2440). ACM.
Ramakrishnan, R., Sridharan, B., Douceur, J.R., Kasturi, P., Krishnamachari-Sampath, B., Krishnamoorthy, K., Li, P., Manu, M., Michaylov, S., Ramos, R. and Sharman, N., 2017, May. Azure data lake store: a hyperscale distributed file service for big data analytics. In Proceedings of the 2017 ACM International Conference on Management of Data (pp. 51-63). ACM.
Rittinghouse, J.W. and Ransome, J.F., 2016. Cloud computing: implementation, management, and security. CRC press.
Starner, T., 2014. How wearables worked their way into the mainstream. IEEE Pervasive Computing, 13(4), pp.10-15.
Zheng, Z., Xie, S., Dai, H., Chen, X. and Wang, H., 2017, June. An overview of blockchain technology: Architecture, consensus, and future trends. In Big Data (BigData Congress), 2017 IEEE International Congress on (pp. 557-564). IEEE.
